Honeypots have long been a staple in the cybersecurity toolkit, serving as decoy systems designed to lure in attackers and study their tactics. However, in the ever-evolving landscape of cyber threats, the question arises: Are honeypots still useful in today's digital world? This article delves into the relevance of honeypots in modern cybersecurity, exploring their effectiveness, benefits, limitations, and best practices for implementation. By examining case studies of successful deployments and forecasting future trends in honeypot technology, we aim to provide a comprehensive overview of the role of honeypots in safeguarding digital assets against malicious actors.
Introduction to Honeypots
Ah, the mysterious world of honeypots! No, we're not talking about pots filled with honey to trap Winnie the Pooh. In the realm of cybersecurity, honeypots are deception tools designed to lure cyber threats and attackers. But are they still relevant in today's digital battleground?
Definition and Purpose of Honeypots
Honeypots are like the secret agents of cybersecurity, pretending to be vulnerable systems to attract malicious actors. Their mission? To gather intel on cyber threats, tactics, and vulnerabilities. Think of them as bait, enticing hackers into a trap where their moves can be studied and thwarted.
Historical Context of Honeypots in Cybersecurity
Honeypots have been around longer than some of those dusty old files on your computer. They gained popularity in the early days of cybersecurity as a way to deceive and outsmart attackers. Back then, it was all about playing mind games with hackers. But in today's ever-evolving cyber landscape, do honeypots still have what it takes?
Evolution of Cyber Threats
As technology advances, so do the cyber threats lurking in the digital shadows. From sophisticated Advanced Persistent Threats (APTs) to the treacherous Insider Threats, hackers have leveled up their game. It's like cyber warfare, with attackers constantly finding new ways to breach defenses and cause chaos.
Rise of Advanced Persistent Threats (APTs)
APTs are like the ninjas of the cyber world - stealthy, persistent, and highly skilled. These sneak attackers can slip past traditional security measures, silently infiltrating networks to steal data or wreak havoc. Dealing with APTs requires more than just a basic antivirus software - it's a whole different ball game.
Emergence of Insider Threats
Watch out for the wolves in sheep's clothing! Insider threats come from within, whether it's a disgruntled employee or a clueless user falling for phishing scams. These threats can be hard to detect since they already have access to the system. It's like trying to spot a spy in your own ranks.
Effectiveness of Honeypots in Modern Cybersecurity
In a world where cyber threats are as common as cat videos on the internet, do honeypots still have a role to play? Can these deceptive tools keep up with the ever-evolving tactics of hackers, or are they just relics of a bygone era?
Detection and Prevention Capabilities
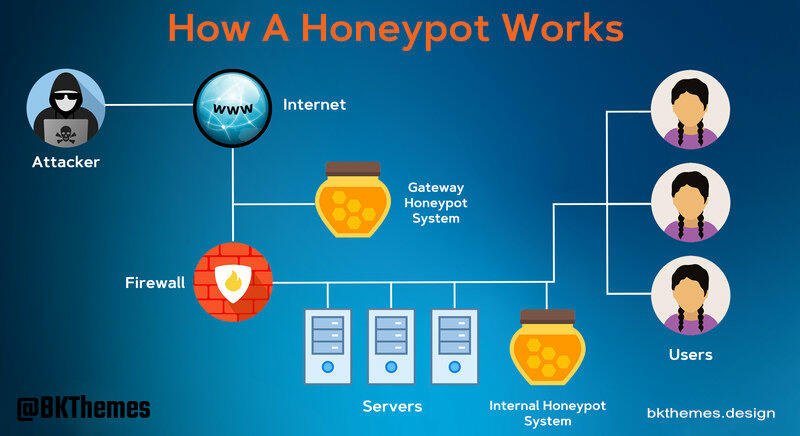
Honeypots are like cyber detectives, sniffing out suspicious activity and alerting defenders to potential threats. With their ability to mimic real systems, they can lure attackers into a virtual trap, buying precious time to analyze their tactics and shore up defenses.
Challenges in Honeypot Deployment
But it's not all rainbows and unicorns in the land of honeypots. Deploying these deception tools can be a tricky business. From setting up realistic decoys to monitoring and analyzing the data gathered, it takes skill and effort to make honeypots an effective part of your cybersecurity strategy.
Benefits and Limitations of Honeypots
So, are honeypots worth the hype, or are they just another shiny object in the cybersecurity toolbox? Let's weigh the pros and cons of using these deceptive tools in the ongoing battle against cyber threats.
Advantages of Using Honeypots
Honeypots offer a unique perspective on cybersecurity threats, giving defenders valuable insights into attacker tactics and vulnerabilities. By studying how hackers interact with these decoy systems, organizations can enhance their security posture and better defend against real-world attacks.
Drawbacks and Risks Associated with Honeypots
But beware, not all that glitters is gold - especially in the world of cybersecurity. Honeypots come with their own set of risks and limitations. From the resources required to maintain and monitor them to the potential for false positives and the risk of attackers turning the tables, deploying honeypots isn't without its challenges.# Best Practices for Implementing Honeypots
Choosing the Right Type of Honeypot
Choosing the right type of honeypot is crucial for its effectiveness. Whether you opt for a high-interaction honeypot that simulates real systems or a low-interaction honeypot that requires less maintenance, consider your goals and resources before diving in.
Integration with Existing Security Infrastructure
Don't leave your honeypot hanging! Integrating it with your existing security infrastructure ensures seamless monitoring and response to potential threats. Make sure your honeypot plays nice with your other security tools for maximum protection.
Case Studies: Successful Honeypot Deployments
Real-World Examples of Honeypots in Action
From catching sneaky cybercriminals to gathering threat intelligence, real-world case studies of successful honeypot deployments showcase the value of these deceptive tools. Learn from others' experiences to fine-tune your own honeypot strategy.
Future Trends and Innovations in Honeypot Technology
Enhancements in Honeypot Design and Functionality
As technology advances, so do honeypots! Keep an eye out for enhancements in design and functionality that make honeypots even more potent in detecting and deterring cyber threats. Stay curious and embrace the evolving landscape of cybersecurity.
Implications for the Future of Cybersecurity
The future is bright for honeypot technology! As cyber threats continue to evolve, honeypots will play a vital role in fortifying defenses and staying one step ahead of attackers. Get ready to ride the wave of innovation in cybersecurity with honeypots leading the charge.
In conclusion,
While the effectiveness of honeypots in modern cybersecurity may vary depending on the specific context and threat landscape, their value as a proactive security measure remains significant. By understanding the benefits, limitations, and best practices associated with honeypot deployment, organizations can enhance their overall security posture and stay ahead of cyber threats. As technology continues to evolve, embracing innovative approaches and staying informed about the latest trends in honeypot technology will be crucial in effectively defending against cyber adversaries.
📧 Stay Updated
Get the latest web development tips and insights delivered to your inbox.




